How to Submit new virus/worm/Trojan samples
Use a program such as TCPview to uncover where the suspect executable(s) are running from (see example below).
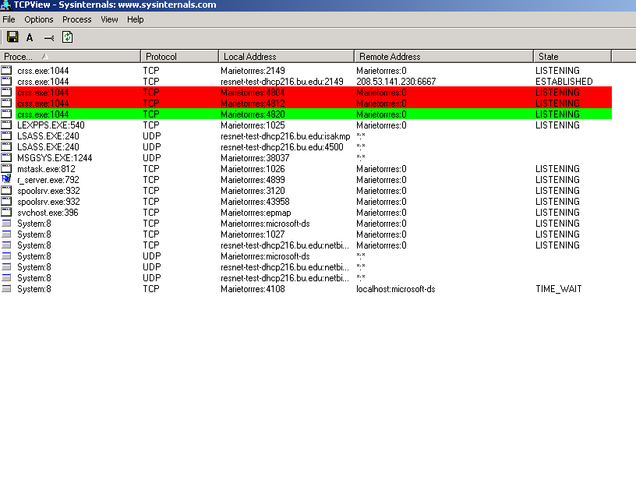
Example of TCPView
From TCPView:
- Right click the suspect process to review theProcess Properties
- Navigate to the folder containing the suspect executable(s)
- Right click on the executable (.exe)
- Select Properties
- Note the creation date and time.
- Use the creation date and time to perform a full search of all local drivesto discover more files that may have been installed with the new virus/worm/Trojan
- Create a password protected (password infected) zip file that contains a copy of all suspect files you have uncovered
Submitting A Sample Electronically
Attach the password protected .ZIP you have created above to an email to virus_research@avertlabs.com with the following information
- What symptoms cause you to suspect that your machine is infected?
- Example: IRT detected virus/worm related IRC sessions.
- Whether any products find a virus (version number, company, results)
- Example: No viruses were found using McAfee 7.1.
- Your Virus Scan information
- Version number and DAT set number
- We are using McAfee ______________________________
- Details that may be relevant about your system
- The system is running Windows ______ with Service Pack _______
- Your name, company name, phone number and email address if possible
- A list of all items contained in the package/message you are composing
- We used Sysinternal’s TCPView Utility to discover the following rogue services were running on TCP ports ______________________ and UDP ports______________________
- We used the creation date of the rogue services to discover all the files installed by the new worm/variant. The zip contains a copy of these files.
